

Become a Certified Digital Investigations Professional in just 10 weeks.
Our platform offers practice, mentoring, peer review, and growth opportunities to current investigators and to those just starting out.
1-on-1 mentoring and instructor assistance
Updated lessons as technology progresses
A focus on building real-world skills

Your Lead Instructor:
Along with other computer and network forensics experts, this program is led by Alex Bray - a senior federal forensics advisor, special forces Sensitive Site Exploitation instructor, former federal task force officer, and former special operations team leader.
As Featured On

Your Lead Instructor:
Along with other computer and network forensics experts this program is led by Alex Bray, a senior federal forensics advisor, special forces Sensitive Site Exploitation instructor, former federal task force officer, and former special operations team leader.
These Courses Cover:

Mobile Device Examinations
Typically containing a wealth of evidentiary information, and located in every subject's back pocket, conducting a proper mobile device exam is vital to modern-day digital investigations. This is typically going to be a Digital Forensic Examiner's bread and butter. In this course, we'll spend a lot of time building up your ability to do a quality mobile device examination.

Computer Forensics
Incorrectly handling a computer on a crime scene can easily result in lost or destroyed evidence. This course gives you the tools to confidently process evidence correctly the first time. This is the area of digital forensics where I most often see examiners making large mistakes that could potentially get the evidence thrown out. In this course, we'll build good habits and discuss common problems.

Incident Response
When a business becomes the victim of cybercrime, the local police department usually has jurisdiction. But do they have the capability to conduct that investigation? It depends. Did they take this course?
This is often the most time-consuming and multi-faceted type of investigation. In this course, we'll give you the skills you need to confidently perform a high-quality network examination.

Sensitive Site Exploitation
Sometimes you can't wait for the evidence to come to you. No, sometimes you have to go get it yourself. The balancing act between being a proficient operator and a professional scientist is tough. In this course, we'll talk about how to best approach that situation and how to achieve this balance quickly.

Crime Scene Investigation
It's important to process crime scenes systematically. Acquiring evidence incorrectly will likely negatively impact the rest of the forensic process. In this course, we'll discuss some important considerations when working on crime scenes either as part of a team, or as the sole technician.

Certification Preparation
In the fields of forensics, law enforcement, and information technology, certifications are vital. As your instructors, we hold multiple, high-level certifications in our fields and, in this course, we'll walk you through some of the most common ones and how to prepare for each.

Digital Investigations Pro is
01 / FAST
Let's be honest here: Most investigations training are 8 hours worth of material presented over 40 hours. That model doesn't work. We have a job to do. So, what if a few industry experts built a massive training library, packed it with high quality material, and then let people take it on their own schedule? Done.
02 / ACCESSIBLE
Want a refresher on a specific process? Need to review a specific topic before court? You used to keep notes and slides from all of your old trainings somewhere in your office. What if you could access the actual lectures AND updated material within the course 24/7, from the phone in your pocket or the computer at your desk? Done.
03 / INEXPENSIVE
Other forensics classes cost well over $3,000 per seat and only cover how to use the course provider's software tool. That's unacceptable. What if there was a certification course that didn't only teach someone a tool, but instead showed them how to effectively use the entire toolbox? Done.
CURRICULUM
With additional material added weekly!
Introduction to Digital Forensics
Introduction
- Welcome
- Your Instructor
- About This Course
- Using the Mobile App
- Course Requirements
- Setting Goals
- Resources
- Equipment and Tool Discounts
- Student Survey
Core Knowledge
- Computer Hardware
- Types of Cables
- Keyboard Shortcuts
- Data Part 1: Binary
- Data Part 2: Hex
- File Systems
- Chain of Custody
- Hashing
- Imaging
- Write-Blocking
- Wear Leveling
- Garbage Collection
- Bruteforcing
- Virtual Machines
- Timelines
- Reporting
- Core Knowledge Assessment (Quiz 1)
Fundamental Processes
- The Digital Forensic Examination
- Case Management
- Digital Evidence Storage
- Best Practices
- Standard Operating Procedure
- Electronic Discovery (E-Discovery)
- Courtroom Preparation
- Courtroom Testimony
Other Topics
- Productivity Tracking
- Laboratory Management
- Audio Forensics
- Vehicle Forensics
- Mental Health
The Toolbox
Introduction
- Welcome
- Mission-Specific Loadout
Free Software Tools
- Magnet RAM Capture
- Hasher
- Arsenal Image Mounter
- FTK Imager
- Autopsy
- Eraser
Paid Software Tools
- Decryption with Passware
Mobile Device Forensics
Introduction
- Welcome
- SIM Cards
- SD Cards
The Mobile Device Examination
- Evidence Preservation
- Types of Mobile Device Extractions
- Mobile Evidence Analysis
- Keywords, Hotlists, Tags
- Reporting
Tool-Specific Lessons
- Cellebrite Intoduction
- Cellebrite Settings
- Cellebrite Other Tools
- Cellebrite Android Extractions
- Cellebrite iOS Extractions
- UFED Troubleshooting
- Cellebrite Physical Analyzer
- Cellebrite Reports
- Magnet AXIOM
Advanced Topics
- Advanced Device Unlocking
- APK Downgrade
- JTAG
- Chip-Off
- Backup Decryption
- File Decryption
Computer Forensics
Introduction
- About This Course
- About Your Instructor
What is Computer Forensics
- Definition
- Training Needed
- Tools Needed
The Investigative Process (CAPER Model)
- Organizational Policies
- Search Authority
- The CAPER Process Model
- Quiz #1
Evidence Collection and Preservation
- Crime Scene Preservation
- Evidence Collection
- Evidence Storage
Acquisition of Data
- Preparation of Laboratory and Documentation
- Drive Geometry, Encryption, and Data Storage
- Acquisition of Data and Hashing
Processing Acquired Data
- Loading Acquired Image into Processing Tools
- Choosing the Right Settings
- Validation of Hash Values
Examining Processed Data
- Identification of Evidence
- Validation of Evidence
- Analysis of Reportable Information
Reporting and Disseminating
- Putting it All Together
- Preparing for Testimony
- Returning the Evidence
- Quiz #2
Core Summary and Exam Preparation
- Cumulative Course Review
Final Exam
Network Forensics
Introduction
- About Your Instructor
- What is Network Forensics?
- Training Needed
- Tools Needed
Networking Basics
- Protocols (OSI, TCP/IP), Internet Protocol and Addressing
- TCP, UDP, Ports
- DNS, Support Protocols (DHCP, ARP)
Preparation
- Incident Response Lifecycle
Investigating Logs
- Windows Event Logs and Sysmon
- Walk Through
- Syslog
- Walk Through (part 1 and 2)
- Firewall Logs
Packet Capture and Analysis
- Capturing Packets
- Wireshark
- Tcpdump
Location Awareness
- Time Zones
- Geolocation
- WiFi Positioning
Finding Artifacts in the Host System
- Windows Services
- Services in Linux and Daemons
- Network Connections
- Tools
Intrusion Detection Systems
- Detection Styles
- Host-Based and Network Based Detection
- Architecture, Alerting
Correlating Attacks
- Time Synchronization, Packet Capture Times
- Log Aggregation and Management
- Timelines
Network Scanning
- Port Scanning, Vulnerability Scanning
- Port Knocking, Tunneling
- Passive Data Gathering
Sensitive Site Exploitation
Introduction
- Welcome to SSE
- Safety and Purpose
- Explosive Ordinance Considerations
- Working in a Non-Permissive Environment
- Physical Fitness
The SSE Process
- Overview
- Order Despite Chaos
- Initiation
- Labeling, Photography, and Sketching
- Volatile Evidence
- Non-Volatile Evidence
- Bag and Tag
Additional Information
- Anti-Forensics
- What's In My SSE Bag?
Military/Law Enforcement Training
For vetted personnel with proper credentials,
we include additional training topics.
WHAT CURRENT STUDENTS ARE SAYING

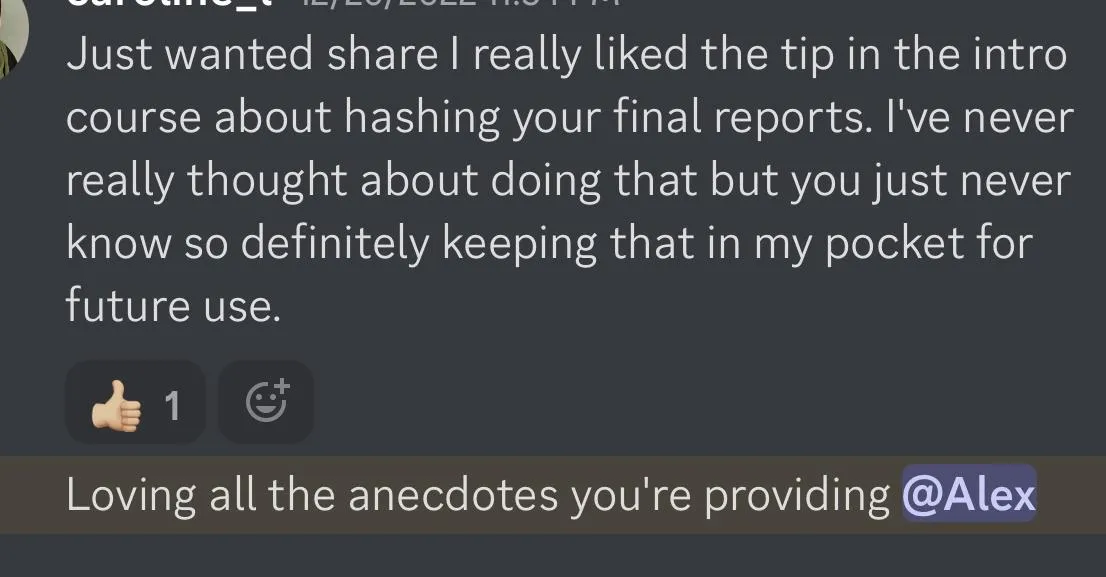
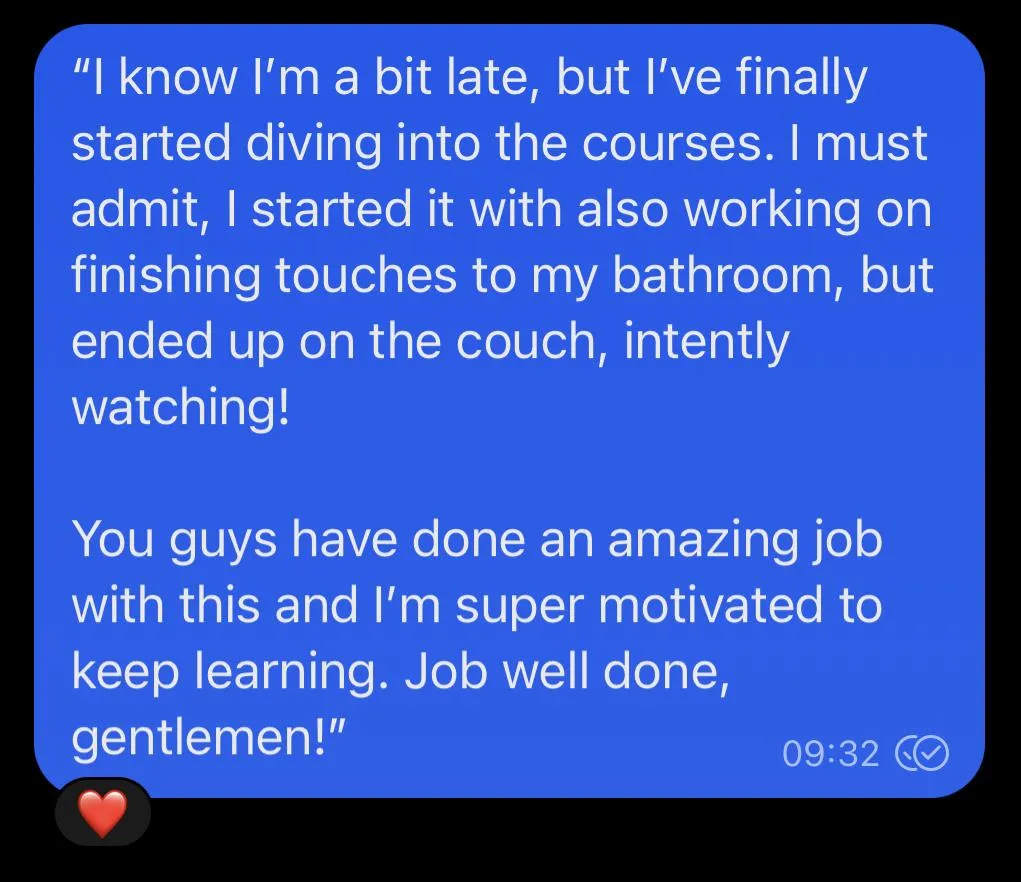
Frequently Asked Questions:
How long do I have access to the course material?
You have 24/7 access to all course material, instructor support, peer community, and technical assistance for the duration of your license.
Is there a mobile app?
Yes! In addition to the website classroom, you can use the app on iOS or Android devices to view lessons and download attachments such as PDF cheat sheets and other resources and guides that we've put together to visualize many of our lectures. You can also message your instructor with questions or comments directly inside of each lesson.
Do you offer certification?
Yes! We offer members an examination attempt towards the Certified Digital Investigations Professional (CDIP), a full-scope certification examination based on a simulated crime. Multiple choice tests don't prove much to anyone. We want to make sure our students are ready for the real world. Members receive one free attempt at the CDIP examination every license period. Members who enrolled with a lifetime access license will have access to the exam once per year at no additional cost.
Is Digital Investigations Pro really covered by a 100% money-back guarantee?
Yes! You get a 30-day money-back guarantee in case this isn't for you. We don't want to sell our program to people who don't need it - so if you go through the course material and decide it's not a good fit, just let us know within 30 days of purchase.
Individual License
1 All-Access License
1 Certification Examination
24/7 Online Training Access
Train at Your Own Pace
No Need for Off-Shift Classes
Regularly Updated Curriculum
New Lessons Added Frequently
Q&A + Mentoring Calls
Quizzes and Exercises
Private Networking Community
Certification Preparation
Review Topics Before Court
PDF Handouts and Resources
FREE Forensics Tools
Agency License
Government Agencies Only
Yearly Subscription
UNLIMITED All-Access Licenses
UNLIMITED Certification Examinations
24/7 Online Training Access
Train at Your Own Pace
No Need for Off-Shift Classes
Regularly Updated Curriculum
New Lessons Added Frequently
Q&A + Mentoring Calls
Certification Preparation
Review Topics Before Court
PDF Handouts and Resources
FREE Forensics Tools
UNLIMITED Accounts
Bulk Pricing for Law Enforcement Agencies
Automatic Access to LE-Only Topics
Need help? Let us know at support@digitalinvestigationspro.com
© 2024 Digital Investigations Pro. All Rights Reserved.
